Back

Malicious-emails
Let’s get this fact out in the open, that cyber-criminals are highly skilled and are experts in devising clever ways to trick the unsuspecting users into their illegal/malicious schemes. Their evil genius is most often the only thing that keeps them out of the reach from authorities.
One of a very notorious scheme by which cyber-crooks trick users and gain their sensitive-data/information is by using spam/malicious-emails. We are all very much aware of spam and promotional emails that do not interest us in any way but sometimes such emails do not pose a cyber-security risk/threat to us.
While on the other hand malicious-emails that are specifically devised to deceive someone to gain the same type of personal information/data without their consent pose more than cyber-security risks/threats, such emails have the capability to cause irreversible damages, not just to our digital-data/information but the implications of such risks can also disrupt our daily life.
CYBERSECURITY-IMPLICATIONS CAUSED BY SUCH EMAILS
There are many different risk-elements that make an email so malicious that it poses a significant security threat to a user. The type of damage caused by malicious-emails depends on the type of security-risk they pose, some of the different types of email-threats include but are not limited to the following (Love, 2017):
An email can contain virus/malware Cyber-crooks can attach deadly virus/malware like zero-day or ransomware to an email that can be hidden in a .rar file or in a link mentioned in the email. And when an unsuspecting user downloads and opens the file or link all of the users data/information present in the IoT-device will get infected/compromised or hijacked.
Fake emails asking for information (Phishing) If their target is a business person, cyber-hackers compose a business email stating to be from a specific department or office requesting to click on a link provided in the email. The links provided in the emails are usually malicious and redirects towards another website that will request some specific data/information from the user to continue the process.
Once a user enters the sensitive-data/information then it is silently obtained by the hacker without being user acknowledging it (Pieter Arntz, 2018). These are also known as phishing-email scams.
Below Figure 1 contains an example of a phishing email sent by a hacker to a student, posing to be from University and request to update the password. In reality, it is nothing more than a trick to get sensitive details of the user, in this case, the student’s password
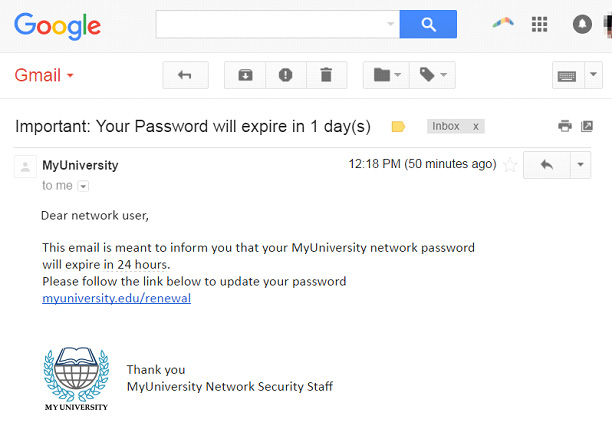 Figure 1:
Figure 1: Fake malicious-email example
An email can contain a Spyware. Specially designed emails by cyber-hackers sometimes attach an innocent-looking file or image, for instance, an image of a pet, that upon being clicked or opened can release a secret spyware-software that can steal a user’s data/information present on IOT-device without raising any suspicion or alerting any antivirus installed.
DEFENDING AGAINST MALICIOUS-EMAILS This is very crucial that we have proper knowledge of how cyber-hackers can steal our private-data/information via emails. Keeping yourself up to date and learning digital-protection strategies will increase individual understanding on how hackers manipulate and craft scams that
most un-educated and less tech-savvy persons fell victim to. Learning about the working and prevention of latest phishing-methods will also help in identifying the email-scams and will provide the required skills to protect our digital-well-being (Irwin, 2019).
The best practice to gain more understanding and knowledge is to search for phishing/scams scenarios and preparing against them. With the right knowledge and skills, we will be able to identify and protect ourselves and others from such malicious-emails and scams.

